DNS Root with accelerated, continually rolling KSK/ZSKs algorithms
RLamb March 2023.
Resurrected Last KSK Roll Mission.
Root server current state indicated by red block in first row. ~60 seconds per slot
To test use resolver config
unbound.conf.txt
and
root.hints.txt.
Set initial unbound.root.key.txt to: . 12 IN DNSKEY 257 3 15 ThisIsAnExampleOnly= This works for me (you may need to change username/port/etc): wget http://a.moot-servers.net/unbound.conf.txt http://a.moot-servers.net/root.hints.txt http://a.moot-servers.net/unbound.root.key.txt; unbound -c unbound.conf.txt -d Then do "dig"s against unbound and see it auto update unbound.root.key.txt
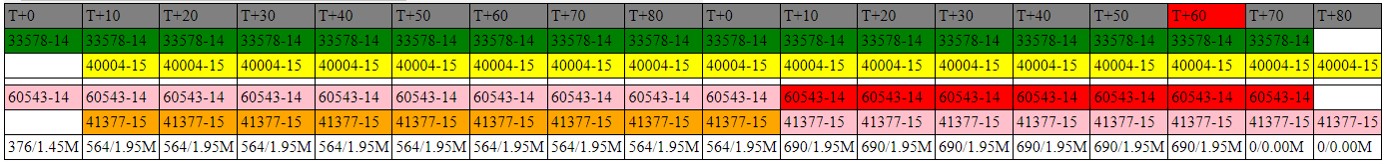
Notes:
- Squares contain key tag number-algorithm number. Rotates thru RSASHA256, ECDSAP256SHA256, ECDSAP384SHA384, ED25519
- Green: current ZSK; Yellow: next ZSK; Pink: current KSK; Orange: next KSK
- Red KSK has revoke bit set in DNSKEY
- Last row is "MSG SIZE" bytes from "dig @me +multi +dnssec -t dnskey ." / signed root zonefile size.
- LIVE Trust Anchors (CSRs, Certs, pgp, pkcs7, xml) as per specification at here or here and draft-jabley-dnssec-trust-anchor
- FYI: Double signing could double the size of the root zone file.
- Accelerated test root is based on real root pulled down once a day.
- Please be nice and dont hit this site/dns too hard! I dont have infinite bandwidth.
Resolver notes:
Not only will you need to set root hints and keys to our test server, but you will also need to set your resolver specific setting for accelerated rfc5011 processing. See https://www.co.tt/files/icksk/ how to. These have likely changed since the first root key rollover. But as fodder for moving forward:
- for Unbound add-holddown: 175, del-holddown: 175. Do "cat unbound.root.key.txt" to see what Unbound thinks is valid (eg "[ VALID|APPEND|REVOKED ]" at the end of keys).
- for Windows Server HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters then Edit -> New -> DWORD and creating TestMode_AccelerateRFC5011Timing and setting the value to 1, and TestMode_AccelerateKeyRolloverTiming and set value to 1
- for Bind start it with command line parameters like: named -c named.conf -T mkeytimers=1/6/180
- for kresd trust_anchors.hold_down_time = 175 * sec, trust_anchors.refresh_time = 10 * sec, trust_anchors.keep_removed = 1
- watch out for algorithm downgrade attack protections when experimenting.
|
Copyright (c) 2023 RLamb
Permission to use, copy, modify, and/or distribute this software for non-commercial use without fee is hereby granted, provided that the above copyright notice and this permission notice appear in all copies. THE SERVICE AND SOFTWARE IS PROVIDED "AS IS" AND THE AUTHOR DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SERVICE OR SOFTWARE INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION, ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SERVICE OR SOFTWARE. |